Step-by-step instructions for startup Nemesida WAF components into operation.
Installation and configuration
Installing the component consists of following all the steps in the manual.
When setting up the filtering node, it is necessary:
1. Check that granted access to external resources;
2. Check that the dynamic module is integrated into the Nginx web server;
3. Check that the version of the installed dynamic module (package nwaf-dyn) corresponds to the installed version of the Nginx web server;
4. Check that the required parameters are set in the /etc/nginx/nwaf/conf/global/nwaf.conf file.
More detailed information is available in the relevant section of the manual.
Checking the configuration
Before checking the operation of the filtering node, you need to make sure that the Nginx web server configuration is correct and restart the services:
# nginx -t # systemctl restart nginx rabbitmq-server memcached nwaf_update mla_main api_firewall # systemctl status nginx rabbitmq-server memcached nwaf_update mla_main api_firewall
If there are no errors when checking the configuration and all services are active, then:
1. Check for possible errors in the logs:
/var/log/nwaf/mla.log;/var/log/nwaf/nwaf_update.log.
2. Check for the file /etc/nginx/nwaf/rules.bin and its size. If the file is missing or empty, then you must provide access to external resources.
3. We are sending a test request:
# curl -i http://WAF_SERVER/nwaftest
If everything is configured correctly, the response from the filtering node will contain the code 403, and a message will appear in the log /var/log/nginx/error.log:
Nemesida WAF: the request 5274fe3c397782a09b4f1b057e572e21 blocked by role ID 1 in zone URL, ...
If the request is not blocked, then follow the steps from the corresponding section manuals.
nwaf-dyn package and basically does not require configuration) and the Nemesida AI MLC machine learning module.
Installation and initial setup
When configuring the component, it must be checked that:
1. Granted access to external resources;
2. The required parameters are set in the /opt/mlc/mlc.conf file;
3. Produced by setting up data collection to build a behavioral model.
Checking the configuration
When checking the Nemesida AI MLC configuration, you must:
1. Restart the services and check their status:
# systemctl restart mlc_main rabbitmq-server memcached # systemctl status mlc_main rabbitmq-server memcached
2. Check for errors in the component log /var/log/nwaf/mlc.log.
Installation and initial setup
When configuring the component, you need to make sure that:
1. Grant access to external resources;
2. The required parameters are set in the file /var/www/nw-api/settings.py;
3. integration Nemesida WAF API with other Nemesida WAF components has been performed.
More detailed information is available in the relevant section of the manual.
Checking the configuration
When checking the Nemesida WAF API configuration, you must:
1. Restart the services and check their status:
# systemctl restart nw-api rldscupd nginx memcached # systemctl status nw-api rldscupd nginx memcached
2. Check for errors in the component log /var/log/uwsgi/nw-api/*.log;
3. Resend the test request to the filtering node:
# curl -i http://WAF_SERVER/nwaftest
If everything is configured correctly, then when the request is blocked by the filtering node, information about the blocked request will appear in the log /var/log/uwsgi/nw-api/nw-api-logging.log:
Updating description for RuleID 1 Request a9d946493221337236b41a7ad0a3120a (BT: 2, client: 1.1.1.1, server: example.com, WAF ID: 1234567890) received from 2.2.2.2
If the entry does not appear, then follow the steps from the corresponding section manuals.
Installation and initial setup
When configuring the component, you need to make sure that:
1. Grant access to external resources;
2. The required parameters are set in the file /var/www/app/cabinet/settings.py;
3. There are no errors when performing migrations and creating an administrator:
Example:
Operations to perform: Apply all migrations: admin, auth, contenttypes, main, sessions Running migrations: Applying main.0001_initial... OK Applying contenttypes.0001_initial... OK Applying admin.0001_initial... OK Applying admin.0002_logentry_remove_auto_add... OK Applying admin.0003_logentry_add_action_flag_choices... OK Applying contenttypes.0002_remove_content_type_name... OK ... Applying main.0091_userconfig_bt16... OK Applying main.0092_geo_tokens... OK Applying main.0093_wafuser_ec_toggle... OK Applying main.0094_alter_geo_tokens_waf_id... OK Applying main.0095_training... OK Applying sessions.0001_initial... OK Superuser's e-mail:
More detailed information is available in the corresponding section of the manual.
Checking the configuration
When checking the Nemesida WAF Cabinet configuration you must:
1. Restart services and check their status:
# systemctl restart nginx cabinet cabinet_ipinfo cabinet_attack_notification cabinet_cleaning_db cabinet_rule_update memcached # systemctl status nginx cabinet cabinet_ipinfo cabinet_attack_notification cabinet_cleaning_db cabinet_rule_update memcached
2. Check for errors in the component log /var/log/uwsgi/cabinet/*.log;
3. Resend the test request to the filtering node:
# curl -i http://WAF_SERVER/nwaftest
If everything is configured correctly, the request that was blocked will be displayed in the Nemesida WAF Cabinet. If the entry does not appear, then follow the steps from the corresponding section of the manual.
4. Activate the Nemesida WAF settings management functionality using the web interface Nemesida WAF Cabinet.
1. Activate the parameters of the monitoring mode (passive mode) of the filtering node in Nemesida WAF Cabinet:
- Activating the request analysis monitoring mode for an IP address:

- Activating the query analysis monitoring mode for the virtual host:

The monitoring mode (passive mode) is designed to prevent blocking requests for the setup period. Activation of the monitoring mode for an IP address is used in cases where it is necessary to exclude blocking when accessing from a certain list of IP addresses (as a rule, from IP addresses belonging to the IT department that configure components), and activation of the monitoring mode for a virtual host eliminates blocking requests for all clients of the web application.
2. Configure the operation of the filtering node as a reverse proxy using the appropriate section manuals;
3. Override matching IP address and domain name so that requests arrive at the filtering node (for example, by editing the DNS A record).
After completing the configuration of the components, the monitoring mode activation parameters must be deactivated and make sure that the protection is active by sending a test request to the filtering node:
# curl -i http://YOUR_SERVER/nwaftest
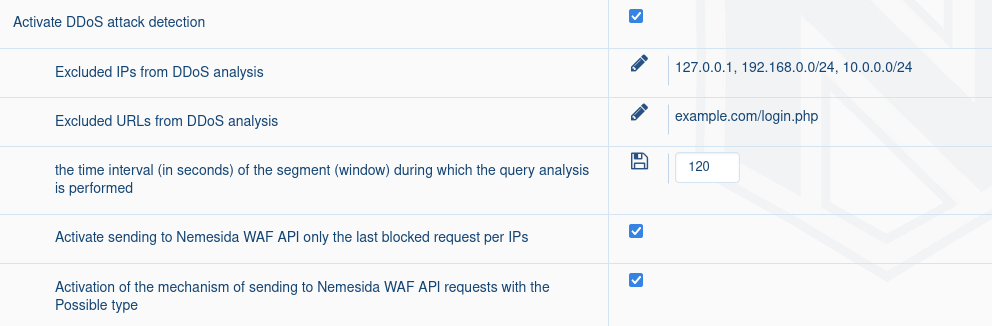
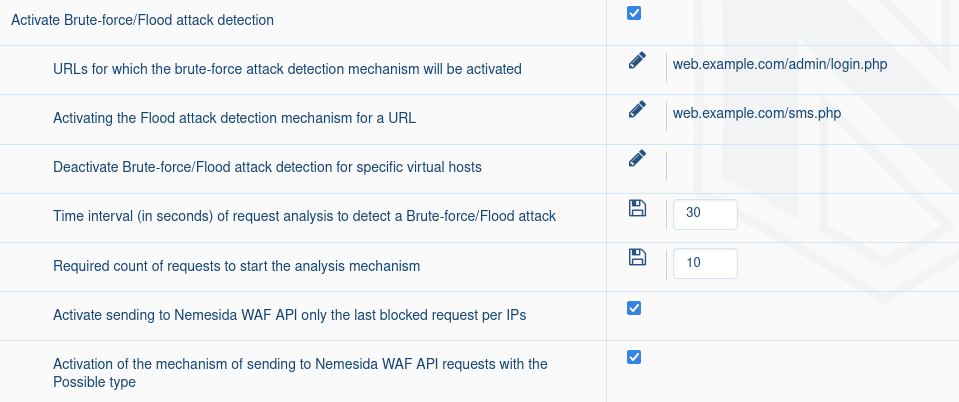
To activate the mechanism for detecting brute force/flood/DDoS attacks and parasitic bots activity by the Nemesida AI machine learning module, follow these steps in Nemesida WAF Cabinet:
- Activate the DDoS attack and parasitic bots activity detection parameters:
- Activate the parameters for detecting attacks using the brute force/flood method:
In case of problems related to the processing of requests by the machine module, follow the steps in the corresponding section of the manual: